Lessons from Trezor breach: hardware vs. custodial wallets

Crypto is a magnet for cybercriminals. They target both custodial and noncustodial services, using hacking and social engineering to steal funds. As conventional banks can block massive transfers at intermediate stages, spectacular heists are now happening in the crypto sphere.
Most incidents occur in the DeFi space. In March 2022, the world saw one of the biggest crypto attacks, with around $600 million stolen from a blockchain connected to the Axie Infinity game. The number of attacks is growing exponentially, causing crypto platforms to ramp up security.
Even owners of hardware wallets are being targeted. The latest phishing attack on Trezor clients, which happened on April 3, reveals important vulnerabilities that users and developers should know.

Trezor data breach
On April 3, 2022, owners of Trezor wallets received emails urging them to install an update. This sophisticated phishing scheme was aimed at stealing assets through maliciously altered wallet software.
Here is how the events unfolded, according to Max Sapelov, CoinLoan CTO. After a concerned wallet owner forwarded the suspicious email, he took action to prevent the hackers from exploiting users.
- The Trezor clients received an email from the trezor(.)us domain mimicking a message from trezor.io. While it bypassed the spam filters and looked legit, it also asked them to update their wallet software (Trezor Suite) by following a link.

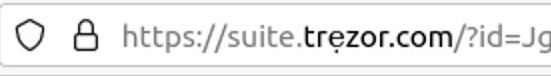
- The link from the email led to a domain that looked like suite.trezor(.)com. Upon closer inspection, it turned out that the domain name included a non-standard character – the Unicode ‘ẹ’ instead of the English ‘e’. Some domain name registrars accept any Unicode symbols, making deceptive lookalike domains possible. Such representation is called Punycode.

Users who followed the link found a copy of the original Trezor site (suite.trezor.io), where they could download fraudulent wallet software. Apparently, this program had been maliciously altered to steal the seed phrase.
After detecting the IP addresses behind the malicious domain, Max contacted the hosting provider, which was located in Russia, and the server was quickly taken down.
- Domain registrars were slow to respond to abuse complaints (it took them around 24 hours), so the scammy domain remained live for quite a while.
- The fraudsters switched to other IP and domain, but Max quickly managed to take down several servers that were hosting the fake Trezor website and distributed malicious software files.
- Finally, Max uploaded the malicious wallet software binaries to VirusTotal, an online service that analyzes suspicious files for malware and automatically shares them with a security community. Only one of the files had been uploaded by that point, which may have indicated a delayed reaction from Trezor.
Trezor’s response
In its email, Trezor blamed the leak on a third-party service – Mailchimp. This veteran email marketing platform confirmed that its database had been “compromised by an insider”.

While Trezor may not be held accountable for the breach, this incident proves that users of hardware wallets are not fully immune to cyber threats. Here are other notable cases when noncustodial wallets were compromised.
Trezor one hack
In January 2022, hacker Kingpin (Joe Grand) cracked the Trezor One wallet of Dan Reich, an NYC-based entrepreneur, to help him recover $2 million in crypto.
In his YouTube video, he explained that he had exploited a peculiarity of Trezor firmware updates. During this process, the PIN key was moved from the flash to RAM, and it was only transferred back upon completion.
The version of the software on Reich’s device merely copied the PIN. This allowed Kingpin to launch a fault injection attack (altering the voltage going to the chip) and bypass the security barriers preventing RAM reading. Here is how he described it:
“We are basically causing misbehavior on the silicon chip inside the device in order to defeat security. And what ended up happening is that I was sitting here watching the computer screen and saw that I was able to defeat the security, the private information, the recovery seed, and the pin that I was going after popped up on the screen.”
The big Ledger hack
Like Trezor, its competitor Ledger has experienced a wallet hack due to a data breach. In July 2020, the company’s e-commerce and marketing database was used to send phishing emails.
While the leaked files did not include payment information, they exposed around 1 million email addresses and other contact details of around 272,000 customers (first and last name, postal address, phone number, and ordered products).
Soon, CoinDesk documented a slew of convincing phishing attacks with emails closely resembling official messages from Ledger.
In 2021, the data ended up on Raidforums, a hacking marketplace that was shut down in April 2022. In response to the incident, Ledger hired a new Chief Information Security Officer, performed multiple penetration tests, and took other measures to enhance security.
New attack vector
In June 2021, some of the victims of the Ledger hack received fake hardware wallets by mail. The parcels appeared to have come from Ledger, and the packaging looked authentic. Each package included a user guide and a poorly written letter with a forged signature of the Ledger CEO.
The guide instructed the user to connect the device to their computer and enter their seed phrase (a string of 12-24 words generated automatically upon wallet setup) into an imposter application. Victims who followed these instructions would lose all of their funds in a flash.
Pros and cons of hardware wallets
It is generally assumed that cold (hardware or noncustodial) wallets are much safer than custodial or CeFi wallets for several reasons:
- The private keys to these wallets are generated directly on the devices and never leave them.
- Users have full control over their private keys.
- Users can double-check all details of each transaction (the destination wallet and the amount) on the display of the device before confirming it.
At the same time, the use of software, connections to third-party vendors, and possible insider leaks point to potential vulnerabilities. As the above cases show, cold wallets expose users to specific types of attacks that custodial services are immune to.
Typically, scammers try to manipulate users into downloading malicious software. Upon launch, it may warn of a vulnerability that must be eliminated via a critical update, and require the seed phrase to confirm it. Once scammers obtain the seed phrase, they gain full access to the wallet and all related private keys.
Safety of custodial wallets (CoinLoan’s experience)
The following is a hypothetical scenario of an attack targeting a platform with custodial wallets. Its users receive phishing emails with links to a legit-looking copy of the original site.
Fraudsters try to obtain access to a particular account (targeted attack) using access recovery procedures.
For this type of attack, fraudsters need to collect the victim’s private information – for example, via social networks or underground services. Then, they typically contact customer support posing as the account holder and request recovery of the lost password and 2FA.
Here is how this attempt would be thwarted on CoinLoan, which boasts a zero-incident track record.
In case of an access recovery attempt, the user is required to complete biometric verification. On CoinLoan, it takes the form of a liveness face check that uses computer vision to detect the presence of a live user and make sure it matches the account holder’s face.
When access to a CoinLoan account is recovered, an automatic withdrawal hold prevents withdrawal for 7-14 days. It is triggered by any sensitive actions, such as changing the password or 2FA. The user is also immediately alerted to them via push notifications and emails sent to all of their internet-connected devices. They have enough time to take action.
Unusual transactions and large-volume transfers trigger the company’s internal risk monitoring systems, so additional biometric verification is required (see above).
CoinLoan uses proven solutions for asset custody and transfers with stringent security policies, including multisignature:
- BitGo – a regulated, qualified custodian with insurance protection that was purpose-built for digital assets;
- Fireblocks – an enterprise-grade platform with a secure infrastructure for moving, storing, and issuing digital assets.
Insider threat is prevented by means of strict internal policies. Sensitive information may only be accessed for specific purposes by a very limited number of employees. Hypothetical theft from wallets is virtually impossible due to the use of multisignature and limits on multiple transaction parameters.
Finally, CoinLoan does not allow 2FA via SMS, as this is the least reliable method.
2FA via SMS as major vulnerability
Most high-profile attacks on custodial services exploited weak access recovery procedures. Hackers who broke into 6,000+ Coinbase accounts in September 2021 bypassed the platform’s 2FA SMS option. They had gained access to the users’ phone numbers. Here is what made such attacks possible:
- Cybercriminals can find a user’s phone number through social media, marketplace sites, and so on.
- After obtaining the number, they can make a SIM swap posing as the victim. The first scenario exploits the opportunity to port a phone number to a device containing a different subscriber identity module. It is also known as port-out scam, SIM splitting, Smishing, and SIM-jacking.
- Fraudsters also exploit SIM card recovery services offered by some mobile providers in the CIS. By posing as the victim and claiming their phone was lost or stolen, they can manage to get a copy of the SIM card.
- Once the phone number gets transferred to the scammer’s SIM, they gain access to the victim’s crypto account via SMS-based 2FA and steal their funds.
Coinbase no longer allows account recovery by SMS. This case shows how weak account recovery procedures can undermine asset safety.
Tips for owners of hardware wallets
Although hardware wallets are still highly secure, users should be aware of phishing and other insidious methods used by social engineers. Such attacks are becoming increasingly advanced. Here are the main precautions:
- Always purchase wallets directly from official stores to avoid getting a fake device with altered firmware.
- Do not store the seed phrase on internet-connected devices. Use a paper or crypto steel to write it down. Store it in a secure place like a safe deposit box. Make a copy for redundancy and store it at another location.
- Never enter your seed phrase anywhere except your hardware wallet device.
- Bookmark the original website in your browser and access it only via the bookmark (not by clicking on any links elsewhere).
- Before downloading any wallet software, double-check the URL of the site.
- Do not make rash decisions. Fraudulent emails often invoke urgency (ask to act now or immediately) to lead the victim to reveal sensitive information promptly.
- Always check the details on the screen of your device (the destination wallet address, amount, and asset) while making a transaction.
Conclusion
Given the potential of social engineering, hardware wallets do not guarantee asset security. Users unaware of the diversity and intricacy of threats can fall victim to manipulation. Wallet owners must take full responsibility for anything that happens with their funds. As the Trezor breach shows, noncustodial wallets are only suitable for tech-savvy users.
Big providers of custodial wallets offer multiple layers of defense and prioritize security reinforcement. Brands like CoinLoan have dedicated teams that block malicious attempts and develop internal policies and tools for account takeover prevention. They protect users from a broad spectrum of threats, conducting multiple checks on their behalf, often unbeknownst to them.
Such custodial wallets are protected against password cracking, access recovery attempts, suspicious transactions, and more. Even non-tech-savvy crypto owners can keep their assets safe with less effort.